
T1.stack
Static stack analysis
based on the executable

Static stack analysis
based on the executable
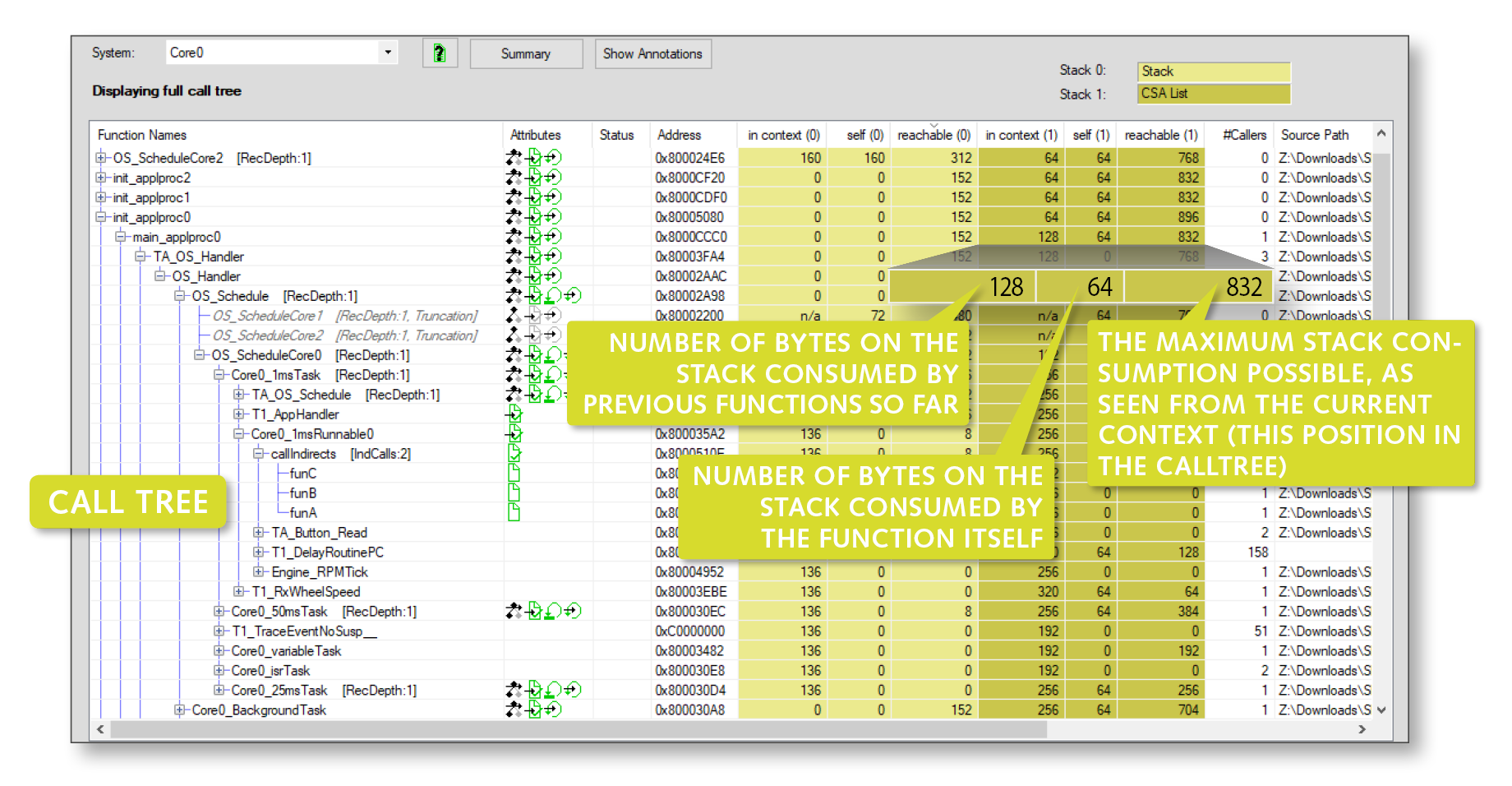
 Based on the binary (the ELF file), T1.stack performs a static code analysis: the binary is disassembled, function calls are extracted and the call tree is reconstructed. At the same time the stack consumption for each function is determined. The call tree and the stack consumption per function are combined into the comprehensive and powerful T1.stack view.
Based on the binary (the ELF file), T1.stack performs a static code analysis: the binary is disassembled, function calls are extracted and the call tree is reconstructed. At the same time the stack consumption for each function is determined. The call tree and the stack consumption per function are combined into the comprehensive and powerful T1.stack view.
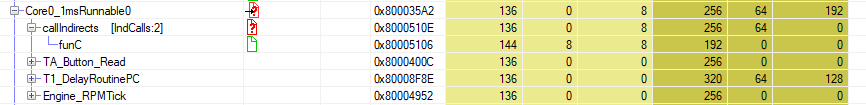
For any static code analysis there are limitations with respect to resolving indirect function calls. Such calls typically use function pointers and it is essential to know all call-targets (functions) which can possibly be called at run-time. T1.stack allows to complete any gaps in the static analysis through annotation. Three kinds of annotation are supported: manual annotation, import of generated annotation files and annotation through T1.flex measurements. Simply measuring call-targets is unique and a highlight of T1.stack. Such measurements can also be used to cross-check and verify annotations from other sources.
Unresolved indirect function call:
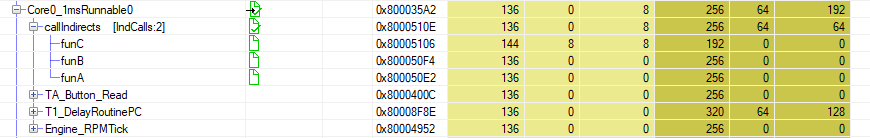
Resolved indirect function call by dynamic T1.flex measurement:
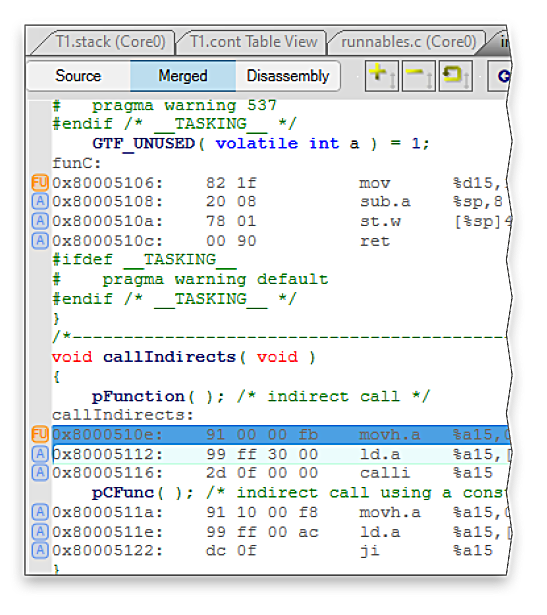
T1.stack offers the advantage of detailed analysis. It detects not only of the amount of used stack but also how and why it is used. Deep understanding of stack consumption allows successful optimization of stack usage and detection of unintended or purposeless use of the stack. Using less stack often helps to improve runtime performance. When using a high level language it is not possible to pre- dict the stack usage from even a detailed knowledge of the C source code. With auto-generated code, the problem is even worse. Using T1.stack, stack consumption can be continually tracked so that the effects of coding and compiler flags can be monitored and understood.
The accurate and detailed analysis of total stack usage combined with validation allows stacks to be reliably dimensioned with T1.stack and thus avoids the waste of allocating unnecessary memory. What's more: stack-overflows can be avoided.
| Silicon/IP Vendor |
Core Architecture | Controller Examples |
|---|---|---|
| Infineon | TC1.6.X, TC1.8 | TC2xx, TC3xx, TC4x |
| NXP/STM | e200z0-z4, z6, z7 | MPC57xx, MPC56xx, MPC55xx, SPC58xx, SPC57xx, SPC56xx, etc. |
| ARM | ARMv7-R: Cortex-R4, R5, R7 and R8 | TI TMS570, Sitara AM6x, TDA4x and DRA8x | Renesas R-Car E3, H3, M3 and V3 |
| ARM | ARMv8-R: Cortex-R52, Cortex-R52+ | ST SR6 Stellar, NXP S32Z, NXP S32E |
| ARM | ARMv7-M: Cortex-M3, Cortex-M4 *, Cortex-M7 * | Infineon Traveo II, LPC17xx, STM32F4xx, Atmel SAM V71, etc. |
| Renesas | RH850 G3K/G3KH/G3M/G3MH/G4MH | RH850/C1x, RH850/F1x, RH850/P1x, RH850/E2x, etc. |
| Intel | x86 64bit | Intel Atom Denverton, etc. |
(*) Cortex-M4 adds DSP and FPU to Cortex-M3. Cortex-M7 further adds a 64-bit bus and double precision FPU. T1 uses the shared sub-set of the instruction sets.